The Palo Alto firewall can block connections from known bad sources. This can be useful for blocking the Delivery or Command and Control stage of a cyber attack lifecycle
Use IP addresses and Address objects in a Security Policy to block traffic
Configure the firewall to use external, third-party IP address lists to block traffic
Configure Anti-Spyware Profiles to block access to malicious domains
Configure Security policy and URL Filtering Profiles to block access to URL categories
Blocking a known bad IP address can be added in the Security Policy Address field.
Blocking a Destination IP address can block connections to a malicious IP address
Blocking a Source IP address can block connections from a malicious IP address
IP addresses can also be created as Objects under Objections -> Addresses. Other type of addressed objects can be an IP Netmask, IP Range, IP Wildcard Mask, or a FQDN.
IP addresses and objects can be grouped under a static address group.
A Dynamic Address group varies from a static address group that tagged IP addresses are automatically added to the group without a commit.
Objects or IP addresses can be tagged by External Software or by Firewall auto-tagging.
The IP addresses in both types of groups can be used in security policies as a match condition for rules.
External Malicious IP Lists can also be used on all firewall models, up to 30 individual lists can be used. Though the maximum numer of IP addresses in total can vary per firewall hardware model.
The maximum amount can be seen if the administrator navigiates to Objects -> External Dynamic Lists and clicking List Capacities.
Some example lists can be found at http://panwdbl.appspot.com
Palo Alto themselves maintan three lists of IP addresses that can be used in Security Policy rules. These are:
- Palo Alto Network – Bulletproof IP addresses
- Palo Alto Networks – High risk IP addresses
- Palo Alto Networks – Known Malicious IP addresses
If an IP address is mistakingly blocked, exceptions can be added.
Other external dynamic lists can be added under Object -> External Dynamic Lists -> Add
A commit operation does not need to be commited each time the IP list requires or has been updated
Mindmeld can be used with Palo Alto firewalls. Mindmeld is an open source tool to input, aggregate, de-duplicate, and output threat intelligence feeds.
The feeds can include malicious IP addresses, domains, and URLS.
Mindmeld shares this list as a webpage that a Palo Alto can access as an External Dynamic List.
Minemeld uses at least 3 nodes to process feeds: A miner, Processor, and Output mode.
The Miner mode accepts a feed input, written for a specific source.
The Processor node aggregates these inputs, and removes any duplicates.
The output node formats the feed and outputs it for a specific target such as a firewall to download as an EDL.
Passive DNS monitoring collects anonymized domain to IP address mapping.
The information gathered from passive DNS monitoring is sent to Wildfire to improve PAN-DB, C2 signatures, and malware detection.
By sharing this information among these databases and signatures, it improves the signatures to detect malicious domains.
This is an opt-in feature, which should be enabled.
Anti-Spyware Security Profiles
Palo Alto distrubute malicious domnain signatures, which are detected with the use of an Anti Spyware Profile. The Anti Spyware Security Profile contains a ruleset to detected and process these threats accordingly.
Malicious domain signature lists are available from many sources accessed as external dynamic lists.
When setting up as an external dynamic list for a Malicious Domain List, it’s type must be set as Domain List.
Malicious Domain Lists can be used from MindMeld
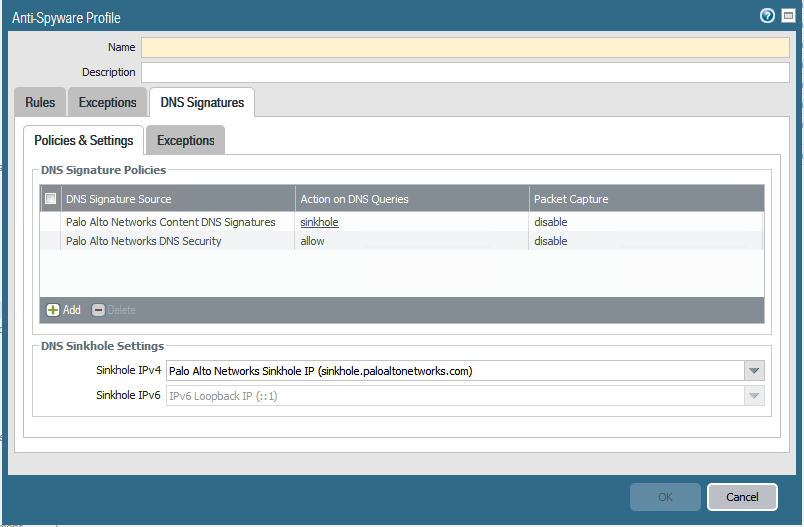
When a DNS query from a client host is received that points to a malicious domain, the Palo Alto firewall responds with a sinkhole address, recording the event in the Threat log.
The host is returned with the IP address of the sinkhole, when the host tries to access this sinkhole address it is logged in the Traffic log.
To configure DNS signature match protection, enter the objects tab and select Anti-Spyware
Add new a profile, select the DNS signatures tab.
Viewing the attempted access of Malicious Domains can be viewed in the Threat Log
URL categories can be used to reduce the attack service of a Delivery or Command and Control stage of the attack life cycle.
There are two methods in accomplishing this, URL categories can be used as a match condition in a Security Policy deny rule or access can be blocked to a URL category in a URL filtering profile.
A security policy deny rule can be used to block access to risky URL categories for most employees.
It is recommended to block command-and-control, dynamic-dns, hacking, high-risk, malware, phishing and unknown.
It is good practice to typically add deny rules towards the top portion of the security policy rules.
URLs denied by the security policy are not logged.
Note that the URL Blocked List has precedence over the Allowed List.
Specific URLs can be blocked by adding them to a custom URL category.
The custom URL category can be attached to a security policy deny rule. Note that individual or specific URLs cannot be attached to a policy rule.
User-ID can be be enabled on the source zone to restrict particular users or groups to policy rules controlling URL category access.
It is recommended to enable logging on the policy rule if the URLs are risky, or to help improve or refine policy rules. Too many hits for example may indicate false positives
URL filtering implements additional security checks on the permitted traffic.
When a URL is checked it is matched against a Security Policy for the following conditions in this order:
- Does the URL match to a predefined or custom URl category, if so, does the rule Permit or Deny this URL?
- If permited, the traffic continues to a URL filtering profile. Does it match to a predefined or custom URL category?
- If so, does the firewall:
- allow
- alert
- continue
- override
- block?
Custom URL lists can be fed into the Palo Alto firewall from MineMeld and other services. Ensure to set the Type to URL List when creating the External Dynamic List.

Leave a Reply