Objectives:
- Describe how a firewall works with WildFire Threat Intelligence Cloud
- Describe how WildFire analysis is used to update URL categories listed in the PAN-DB URL Filtering data
- Configure Session Information Settings to specify which type of session information will be sent to Wildfire
- Define a WildFire Analysis Profile
- Configure both the types of information submitted to WildFire and the amouht of information is returned to the firewall in the report
Evolution of Malware
In modern times malware has evolved.
Instead of being a simple replication of a virus, it has adapted to be highly evasive and adaptable to avoid deteciton. Highly targeted and sophisticated when launching attacks
This new breed of malware that is often the core of the most sophisticated attacks on organisations networks today
Often this new malware is customised for a particular attack, making it more difficult for traditional signature-based anti-malware solutions to detect it
WildFire Threat Intelligence Cloud`
Palo Alto firewalls arouind the world automatically forward unknown files and URL links found in emails to the WildFire Threat Intelligence Cloud Cloud, or one of the three regional clouds for analysis.
The three regional clouds are in Europe, Japan, or Singapore.
Each cloud analyses samples and generates malware signatures and verdicts independently of other WildFire clouds.
The sample could be detected as Benign, Grayware, Malware or Phishing. If Phishing the PAN-DB URL Database will get updated.
WildFire signatures and verdicts are shared globaly which allow WildFire users to benefit from the anti-malware coverage no matter where they are in the world.
WildFire users can also use the WildFire XML API or WildFire Dashboard to manually upload files to WildFire for analysis.
Recap of Wildfire
WildFire is a cloud based virtual sandbox used to evaluate unknown files and URL links found in e-mails.
The evaluation occurs for Android, Linux, MAC OSX, Windows XP, Windows 7 and Windows 10
If malware or phishing is founmd, WildFire creates a new antivirus signature or adds the URL to the PAN-DB Phishing URL category.
These updates are available in minutes for firewalls around the world to download.
Overview of Wildfires Operation
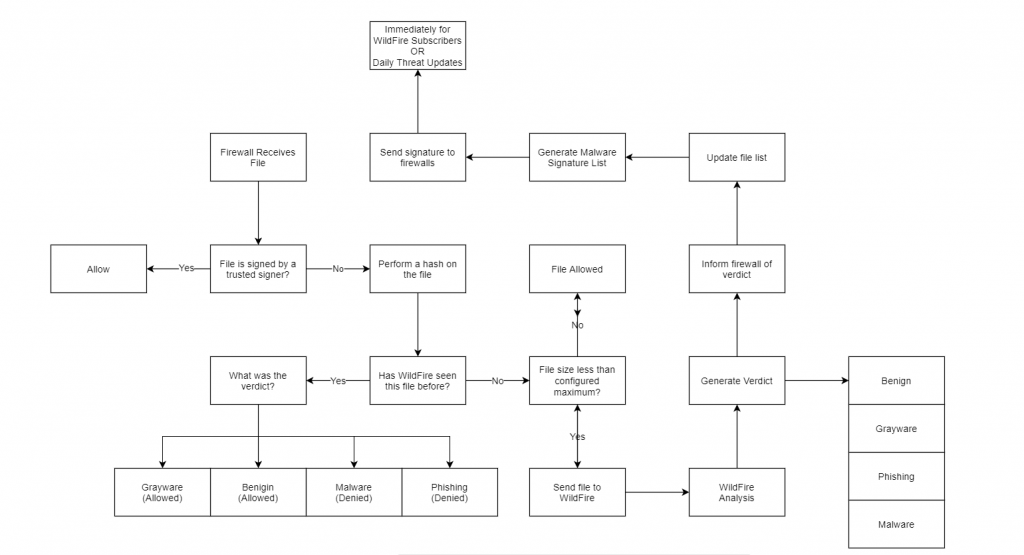
For the daily threat updates, the new signature is normally delivered within 24 to 48 hours
WildFire Verdict Descriptions
Benign
Safe and does not exhibit malicious behavior
Grayware
No security threat but may display obtrusive behavior
Malware
Malicious in nature and intend and can pose a security threat
Phishing
Based on properties and behaviors the website displays
WildFire Protects E-mail
The Palo Alto firewall has the capability to send email attachements or URL links to WildFire for analysis.
The firewall nor Wildfire store or enable viewing of the email contents.
If WildFire detects a malicious file, it immediatly creates a new anti-virus signature that can be downloaded by Palo Alto firewalls around the world.
This new antivirus signature can help prevent further compromise of other machines in the network and around the world.
If the firewall has a WildFire and PAN-DB licence, the firewall can gain access to the signatures in as little as 5 minutes.
If WildFire determines a file attachment or e-mail URL link is malicious, it includes the email header in WildFire Submissions logs that it returns to the firewall. If User-ID technology is eanbled, the log can be used to quickly find and remediate the threats received by the user.
Content Packages and Wildfire Updates
WildFIre analysis is used to create new antivirus signaturtes.
It also is used to update the URLs and URL categories listed in the PAN-DB URL Filtering database.
Antivirus signatures are made available within 24 to 48 hours as content updates to the Antivirus content database.
Daily downloads of the antivirus content database can be scheduled. Firewall access to the AntiVirus content database is permitted with a Threat Prevention Licence.
Antivirus signatures are also available as little as 5 minutes as content from the WildFire Signatures database. A firewall can scheduled as little as every minute to check for updates. Access to this database is permitted with a WildFire licence.
URL updates are available within 5 minutes as content updates to the PAN-DB URL Filtering database.
Updates of the firewall with new content updates of the PAN-DB URL Filtering do not need to be scheduled, as new URL information is downloaded dynamically as needed.
Firewall access to the PAB-DB URL filtering database is enabled using a URL Filtering Licence.
Standard and Licensed Functionality
Standard Subscription
- Windows XP and 7 analysis
- Windows PE file analysis
- EXE, DLL, SCR, FON, and others
- Antivirus signatures delivered by daily dynamic content updates (requires Threat Prevention licence)
- Automatic file submission
WildFire licensed service
- Standard subscription features
- Additional file type analysis:
- Microsoft Office extensions, PDF, JAR, CLASS, SWF, SWC, APK, Mach-O, DMG, RAR, 7-Zip, Linux ELF, PKG
- WildFire signature updates every 5 minutes
- API file submission
- WildFire private cloud appliance
- WF-500
WildFire Licenses
Signatures
There are two different content package formats for WildFire content updates, content packages for 7.1 and later, and content packages for 7.0 and earlier.
The content packages contain the same set of signatures
XML API
A licence allows users to submit files for analysis to WildFire using the WildFire XML API
Private Cloud
A WildFire licence entitles a firewall to use the WF-500 appliance as a WildFire private cloud service.
WildFire Private Cloud
The WF-500 is a WildFire private cloud solution. It supports Windows XP and Windows 7 virtual environments and requires a Windows 7 64-bit image to be installed on the appliance.
The WF-500 locally analyses unknown files, plus files and URLs found in email.
The advantage being that these files will never leave your network.
The WF-500 does not support scanning of APK files.
The WF-500 locally generates antivirus signatures and categorises URLs.
The administrator can choose whether to automatically forward malware files to the public cloud for signature generation.
The WF-500 appliances supports the WildFire XML API.
Content updates to the WF-500 are provided daily, helping to imrpove analysis accuracy. Trusted code-signing certificates, malware domain lists, new signatures are examples of content packages provided to the WF-500 via updates.
The WF-500 can be configured to provide automatic download and installation of WF-500 content packages, or can be manually accomplished by an administrator.
Hybrid Cloud
The Hybrid Cloud combines the public and private cloud solutions.
If a WF-500 applioance is used, a WildFire hybrid cloud can be enabled that lets the WF-500 analyse sensitive file types locally, whie less sensitive file types are sent to the WildFire public cloud.
Files that are not supported on the WF-500, such as APK, can be set to be forwarded to the public cloud.
If public and private cloud solutions have configuration overlap, the private cloud analysis will prevail.
WildFire Appliance Cluster
Up to 20 WildFire appliances (WF-500) can form a WildFire appliance cluster on a single network.
Clusters are useful where the WildFire public cloud can not be used.
The larger clusters have better support for a larger firewall deployment on a single network over the capability a single WildFire appliance provides.
Wildfire clusters also provide fault tolerance, and a single signature package is provided to all firewalls connected to that cluster.
Encryption can be enabled on appliance clusters too, beginning with PAN-OS 8.1.
Encryption can be switched on to maintain confidentiality of transmitted content.
Clusters can be operated in a FIPS/CC environment where they are configured using FIPS/CC compliant certificates.
WildFire Analysis Profiles
WildFire analysis profiles are objects that are added to security profile rules that are configured with an action of “allow”.
WildFire analysis profiles are not required for security profile rules with the deny action, because no further processing is needed of traffic that will be dropped.
WildFire Analysis are applied to all packets during the life of a session.
WildFire anaylsis profiles represent additional security checks on files in allowed network traffic.
WildFire analysis profiles allow more granular control over allowed traffic.
An example is that the firewall can be configured to submit files to Wildfire only when a specific file type is matched, and they are transferred in a specific direction by a specific application.
Files submitted by WildFire are logged to Monitor -> Logs -> WildFire -> Submissions
The firewall contains a pre-defined, read only default WildFire Analysis Profile.
It can be customised by creating a new WildFire profile, or cloning the default profile and editing that clone.
The default profile rule sends all unknown files from any applications allowed by the rul,e to the WildFire public cloud for analysis.
WildFire Reporting Overview
Each time that the WildFire technology analyses a file or URL link, it will report it’s finding to the firewall.
The administrator can configure the information submitted to WildFire and the amount of information that is returned to the firewall in the report.
Information reported back to the firewall is recorded by the firewall in the WildFire submissions log.

Leave a Reply