These are rough notes on my study of Palo Alto Firewalls, expect bad writing!
Describing what happens at each of the seven stages in the cyber-attack lifecycle
Stage 1: Reconnassisance
Attackers research, identify and select targets. This can carried out via typical phishing tatics or mining data from LinkedIn profiles or coprorate websites. Scanning the network for vunerable services or applications that the attacker is another form of reconnassisance.
The methods of reconnassise can be divided into two catogaries, passive and active.
Passive methods search for available information without interacting with the target network, or at least in a way that would not be deemed suspicious.
One passive method would be social engineering. An example could be searching a target user on a popular social network site such as LinkedIn, learning about their hobbies to try improve the success rate of a phishing attack.
Active methods involve actively interacting with a target network to determine information about it. An active method is likely to raise suspiciouson if the attacker is picked up on.
A number of examples of active methods are include:
Host Sweeps – Ping ranges of IP addresses to gain fingerprint information of devices that respond, or do not respond.
DNS Lookups – Discover IP addresses of and public services of a company by looking up DNS records assicioated with that company. This stage could be followed up with a host sweep or port scans.
Palo Alto firewalls have several features to defend against, preventing, or mitigating active reconnaissance.
Network Segementation into zones
Zone Protection Profiles
External Dynamic List (EDL)
Security Policy Rules
Stage 2: Weaponisation
The attackers choose their method of attack, and develop the malware used to initiate that attack. The network/security administrator can’t act on this stage since the activity happens outside of the realm of the organisations network
The malware is designed to exploit a software vulnerability discovered duringt he reconnaissance stage, this can exist in an operating system, network service, or application.
Stage 3: Delivery
Malware is delivered at this stage and designed to exploit existing software vulnerabilities. The attacker may choose embed malicious code in what appears to be legitimate PDF or Word files. An alternative method might be that the attacker will try the victim into accessing a malicious website to deliver the malware payload.
Stage 4: Exploitation
Once the malware has been delivered, it’ll run the attack code that exploits the vulnerabilities on the victoms devices. The code is designed to gain enough access priveileges on the victims device to open an entry point to download and install more sophisticated and damaging malware at the next stage of the attack.
A Palo Alto firewall can prevent the delivery of detected malware that passes through it’s network stack.
If a user brings the malware into company, say on a laptop or usb infected device that does not pass through a firewall, the detection and block method is likely left to any endpoint protection (a locally installed anti-virus)
Stage 5: Installation
The attacker has now gained sufficient privilages from the initial malware delivery. Now downloading further code to gain full and access and control to the device and it’s files it no longer needs to rely on the existing operating system, applications, commands and executables. Providing the attacker with a broad range of powers to modify the behaviors of the compromised device
To establish a consistent method of access, the malware often installs a backdoor to allow the attacker to access the device even if passwords are changed or services are disabled. The back-door is likely created through the use of a kernel, firmware-based rootkit or remote administration tool.
In order to block an attacker at this stage, firewall protections can be configured that can block access to the attackers installation server, or block file downloads from the installation server. An example could be to only permit known application traffic, or controling access to only known and permitted categories of websites. File Blocking Profiles or WildFire profiles can also help block the attacker. An extra layer to assist with these technologies would be the use of decryption and inspection of encrypted web traffic (https).
Stage 6: Command and Control
With the full malware package now installed, attackers will often establish a communication channel back through the internet to a central command and control server, allowing easy future access for the attacker to remotely control the computer. The channel often uses a DNS domain name to resolve the IP address of the control host. The use of DNS allows the attacker to easily move from one IP address to another, so they can avoid an IP block list.
The communcation channel (C2 channel) can be used to update the malware with new functionality as the attackers objectives change, or give the attacker control of the compromised host to change the appearance of the malware.
Changes to the functionality, and appearance can modify the malwares signature so that antivirus scanners are not able to detect the malware from it’s their known signature list.
Similar to the installation stage, Palo Alto firewalls can help prevent giving an attacker access by only permitting known application traffic, preventing access to unknown websites and domains along with blocking access using external dynamic lists. Decryption and inspection of encrypted traffic can aid other firewall technologies in accomplishing this goal
Stage 7: Act on the Objective
Attackers may have different motivations for the attack they carry out – not always being for monetary profity. The reasons could include exfiltrating data, destroying infrastructue, defacing web property, creating fear, extortion, or a polictical or social statement. The infected device might not be the target of the object, but rather a point of attack to the intended target.
The firewall can provide a number of features to obstruct an attackers objective, an example being File Blocking or Data Filtering profiles could block and prevent data exfiltration
Describe the characteristics of commodity threats, advanced persistent threads (APTs), and denial-of-serivce (DoS) threats
Most threats seen today are commodity threats, being opportunistic or targeted.
Some risks are benign such as Adware, and others being serious such as ransomware or rootkit.
Advanced Persistant Threats are seen as the most dangerous type of threat due to the undected, long-term access to sensitive data.
The danger is the result of the poissible damage caused by undetected long term access to sensitive data.
Considered advanced due to likely being perpetrated by highly motivated and well funded attackers.
Attackers use sophisticated knowledge and techniques to gain unauthorised access to monitor, steal, corrupt or delete data.
An advanced persistant threat can utilise commodity threats as part of their attack
The persistance comes from the attacker extering a continious effort to gain unauthorised access, using a varierty of techniques to disguise their activity.
The techniques of hiding activity can come in the form of a firmware-based rootkit or remote adminstration tool. These two techniques are an example of allowing the atrtacker to hide their command and control (C2) communications.
Since the attacker can hide their command and control commuincations, this enables the attacker to modify their malware to avoid detection and change the purpose of the malware to suit their objectives.
An advanced persistant threat can be difficult to defend against since it may use multiple attack vectors to compromise and maintain communication with an infected device
The attacker may use various types of malware (rootkits, remote administation tools, worms, trojans), various social engineering attacks (phishing campaigns, watering holes) or various attack methods (man in the middle attacks, denial of service attacks)
Attacks are often begun by compromising a trusted business parter of the actual target and then using the business partners network access to attack the target.
A denial of service attack is an attempt to disrupt access to data and network services by overloading the network or a server with unnecessary traffic.
Motivations for such an attack may include political or social activsm, for a hacker group to gain notoriety or disrupt a competitor.
Palo Alto firewalls contain a couple of features to defend against denial of service attacks, zone protection profiles provide broad based comprehensive denial of service protection to protect an enterprise from volumetric denial of service attacks. Acting as a first line of defence for the network. Another feature is Denial of Service Protection policy and Denial of Service Protection Profiles. These provide flexible rules and matching criteria to help protect destination zones or specific end hosts. The protection policy or profile is suited to protecting servers that are critical or historicaly prone to denial of service attacks
List examples of firewall threat preventions available at each of the six stages in the firewall packet flow
Sessions and Flows
The firewall inspects data payloads as part of a session, each session as a unique session ID number. Each Palo Alto Firewall model and each of it’s virtual systems has a supported maximum number of sessions.
The maximum number of sessions is reported on the web interface dashboard, along with the number of sessions currently active.

The endpont that initiates the connection is the client, and the endpoint that responds is the server.
A Client to Server rule, must be specifically enabled using a security policy rule.
Return Server to Client traffic is automatically permited, and does not need to be considered for sueciry policys.
A flow is idenitified by using a combination of source and destination IP address, ports, and the protocol in use.
Each flow is assigned a unique flow key, and each flow key is assigned a session ID number
Stages of Packet Flow:
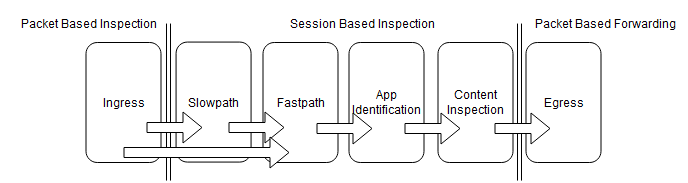
- Packet Based Inspection
- Stage 1: Ingress
- Recieves Packets
- Detects and drops packets with errors
- Detects and blocks pression packet-based attacks
- Stage 1: Ingress
- Session-Based Inspection
- Stage 2: Slowpath
- Establishes new sessions
- Checks FW session limits
- Performs session-based DoS protection
- Checks and applies Security policy rules
- Stage 3: Fastpath
- Performs NAT and decryption
- Performs session-based DoS protection
- Checks and applies Security policy rules
- Stage 4: App Identifcation
- Identifies applications
- Checks and applies Security policy rules
- Stage 5: Content Inspection
- Performs threat inspection and takes action prescribed in Security Profiles
- Re-encrypts decrypted traffic
- Stage 2: Slowpath
- Packet-Based Forwarding
- Stage 6: Egress
- Implements Quality of Service Policy
- Forwads the packet to the next destination
- Stage 6: Egress

Leave a Reply